Difference between revisions of "Transmission Module"
| Line 116: | Line 116: | ||
'''After''' | '''After''' | ||
[[File:Transmission Module Section After(1).PNG| | [[File:Transmission Module Section After(1).PNG| 1000px]] | ||
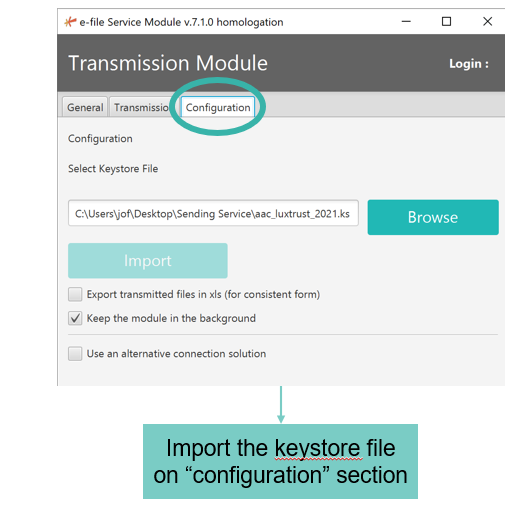
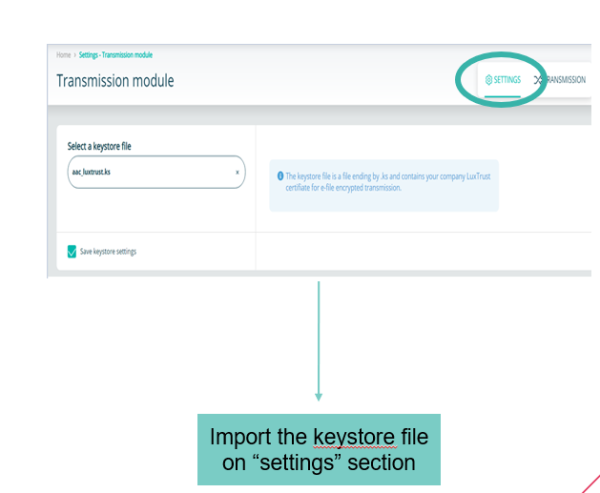
=== Keystore Selection === | === Keystore Selection === | ||
Revision as of 14:03, 14 September 2021
Operating mode
Main functionalities of the Transmission Module:
- Encryption and decryption of documents
- Transmission of documents to supervisory authorities
- Keystore generation
- Certificate Request generation and activation
System requirements
e-file is compatible with all Windows and Mac Os versions.
Reporting services using www.e-file.lu
| Additional information | |
|---|---|
| Proxy, antivirus | Your system (proxy, antivirus,...) must allow .jar and .jnlp files to be downloaded The ports 80 (HTTP) and 443 (HTTPS) must be enabled as well as those technical URLs : www.e-file.lu/WSEfileFlex, www.e-file.lu/WSEfile, www.e-file.lu/ECH |
| Read and write access to e-file working folders | The Transmission Module needs read and write access to e-file working folders. Therefore, the keystore is imported by default in the "workdir" directory on the C:\ drive: C:\Users\<username> \efile\workdir. |
| Cookies | Cookies have to be enabled How to enable Cookies |
| Web browsers | e-file is compliant with most current browsers. Please call us if you have a particular configuration. |
| Chrome |
The default installation of Chrome works correctly. |
Edge Chromium 
|
The new Microsoft Edge is based on Chromium and was released on January 15, 2020. It is compatible with all supported versions of Windows, and macOS.. |
Internet Explorer  |
(-) At least Internet Explorer version 11 needs to be installed on your computer.
(-) 'Do not save encrypted pages to disk' has to be unchecked. |
Firefox 
|
The default installation of Firefox works correctly Please refer to the section : Firefox and Safari compatibility. |
Safari 
|
The default installation of Safari works correctly Please refer to the section : Firefox and Safari compatibility.
|
Luxtrust certificate
| Additional information | |
|---|---|
| LuxTrust certificate order | For encryption purposes, a Luxtrust SSL certificate is mandatory to use our services. To be able to order the certificate on Luxtrust’s webpage www.easyssl.lu you need to use a modern browser (Chrome, Firefox, Safari, IE10 ...) |
Manual file transmission
Our Transmission Module allows you to submit reports and documents to Luxembourg authorities.
Transmission Module Migration
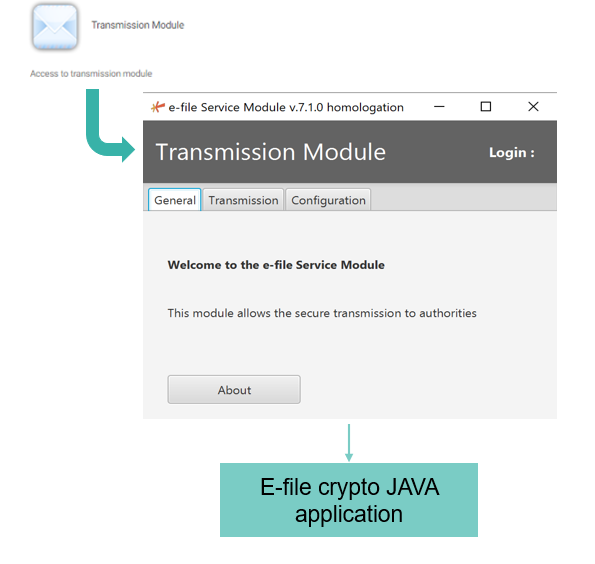
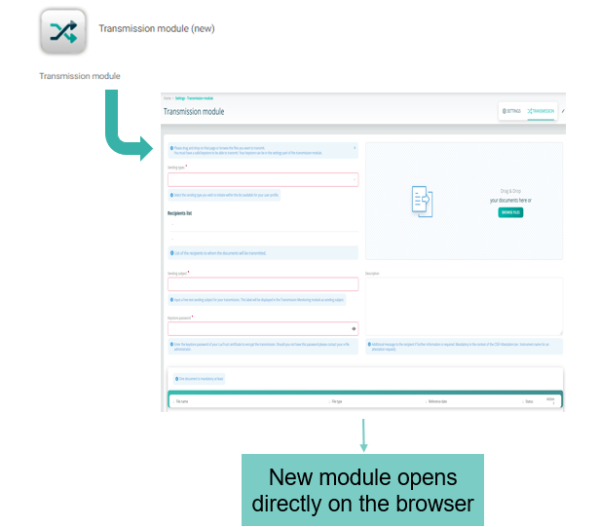
E-file Crypto JAVA application is replaced by a new transmission module application that opens directly in the browser.
Transmission Module Technologie
Before
After
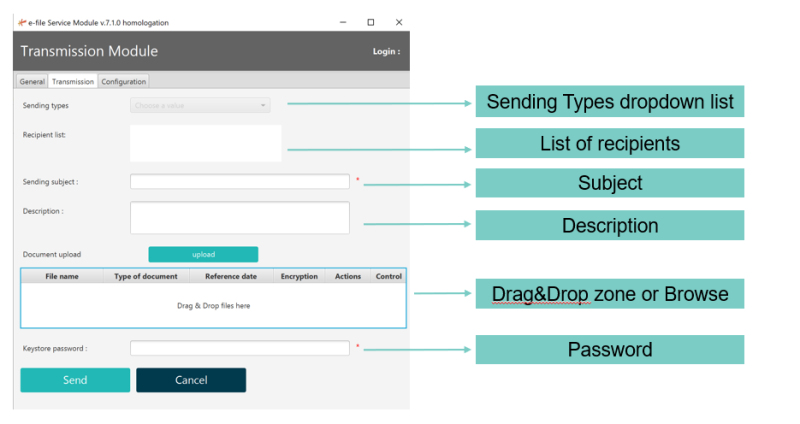
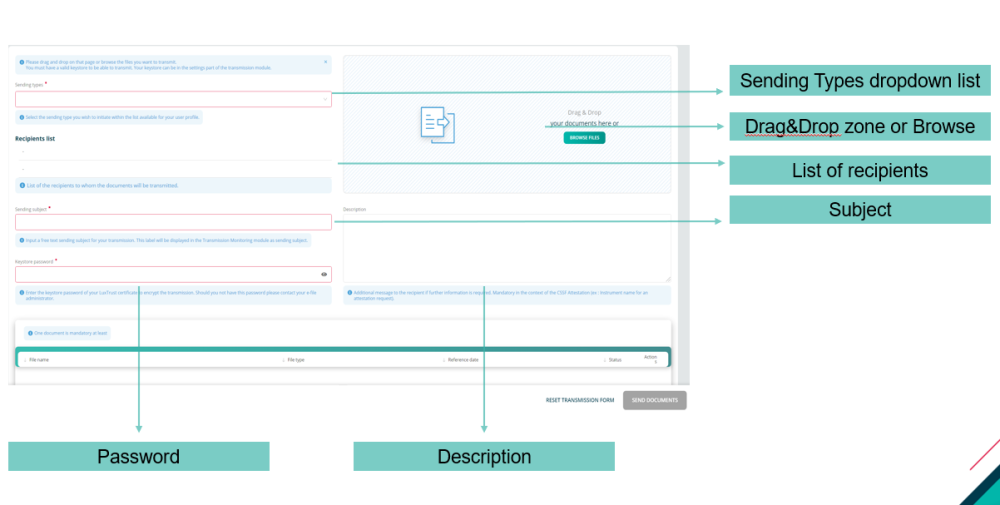
Transmission Section
Before
After
Keystore Selection
Before
After
Sending types
| Sending type | Reporting | Example | Detailed information | Internal technical business ID |
|---|---|---|---|---|
| MMF reporting | MMFREP | MMFREP-P00000789-O00000654-00000123-2020-Q1-0001.zip MMFREP-P00000789-O00000654-00000123-2020-Y1-0001.zip |
CSSF - Money market fund |
bus 83 wkf 131 |
| Mifir reporting | TAFREP | TAFREP-B00000001-2017-04-15-123456.xml | CSSF - TAF Handbook | bus 71 wkf 111 |
| Reporting IORP | SUFREP | SUFREP-ENNNNNNNN-TJJJJJJJJ-SSSSSSSS-YYYY-MM-R-TTTTTT-LL-C-D-S.zip | (-) CSSF - Legal reporting (-) CIRCULAR CSSF 19/726 |
bus 80 wkf 130 |
| AnaCredit | ANTREF ANTT1M ANTT2M ANTT2Q |
ANTREF_201801_LUB00999_20180205-001.xml ANTT1M_201801_LUB00999_LUB00999_20180205-001.xml ANTT2M_201801_LUB00999_LUB00999_20180205-001.xml ANTT2Q_201803_LUB00999_LUB00999_20180405-001.xml |
BCL - Reporting instructions | bus 74 wkf 122 |
| SHS-Group reporting | SHSGRP | SHSGRP_201709_LUB00999_20171206_001.xml | BCL - Reporting instructions | bus 75 wkf 123 |
| FINREP report | B2.4 B2.5 |
FRCREP-B9999-2007-12-B24-L2-L-N--B24.XML FRCREP-B9999-2007-12-B24-L2-L-N--.zip |
Naming convention for CSSF reportings | bus 73 wkf 86 |
| Reporting EDIFACT | B4.4 (Credit institutions) | B0001809.T01 | (-) CSSF - Reporting instructions Edifact B4.4 (-) Naming convention for CSSF reportings |
bus 73 wkf 86 |
| Reporting CSDR | CSDREP | CSDREP-B00000001-B00000001-2018-Q4-20190101-1.zip | (-) CSSF - Circular 19/709 |
bus 78 wkfxxx |
| COREP report | COFREP | COFREP-B00000999-2014-03-CCOREP-00-L-N-S-CCOREP.xbrl COFREP-B00000999-2014-03-CCOREP-00-L-N-S.zip COFREP-B00000999-2019-12-SRESOL-00-L-N--.zip |
(-) CSSF - Reporting requirements for credit institutions (-) Naming convention for CSSF reportings |
bus 72 wkf 85 |
| Credit institution reporting | AR: Annual Report AS: Annual report consolidated CO: Compliance Report GR: Governance Report IA: Internal Audit Report IC: ICAAP ID: ICAAP Consolidated LF: Long Form Report LC: Long Form consolidated LD: Long form branch or specific participation RR: Results distribution
|
DOCREP-B00000998-00000000-0000-2009-12-31-LG-EN-0000.pdf |
bus 27 wkf 92 | |
| BCL statistics | S0.1; S1.1; S1.4; S1.5; S1.8; S1.9; S2.5-L; S2.5-N; S2.8; S2.9-L; S 2.9-N; S3.2 |
S0001_L1_20130616_B000000999_B000000999_20130617_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 13 wkf 96 |
| Reporting S1.12-L | S1.12-L | S0112-L_L0_201905_B000000999_B000000999_20130605_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 76 wkf 124 |
| Security by security Banks | TPTBBL; TPTBBN; TPTBHR; TPTBHN | TPTBBL_L4_201804_B000000999_B000000999_20180617_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 20 wkf 97 |
| Payments balance | BOP | BOP101_20130616_B000000999_B000000999_20130617_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 12 wkf 105 |
| CSSF enquiry | ESPREP | ESPREP-B0999-2008-06-STT.xls | (-) Naming convention for CSSF reportings | bus 15 wkf 78 |
| EDP report | EDPREP | EDPREP-Z9999-2011-03-Z11-L0-L-N--.xls | (-) CSSF - Reporting instructions |
bus 29 wkf 109 |
| EME report | EMEREP | EMEREP-W9999-2011-03-W11-L0-L-N--.xls | (-) CSSF - Reporting instructions (-) Naming convention for CSSF reportings |
bus 34 wkf 110 |
| Data payment collection (CDP) | V1.1 - V1.14 | V0101_L2_201601_W000000003_B000000999_20160201_001.xml | BCL - File name convention | bus 36 wkf 74 |
| Reporting U | U1.1 | U11REP-B00000012-O00008450-00000002-201512-RAP-1421893257541.xml | (-) CSSF - Circular 15/627 |
bus 8 wkf |
| Reporting Sicar | SICREP | SICREP-B999999-K999990000-2008-06-K31-L0-L-N.xls |
(-) CSSF - Circular 08/376 |
bus 17 wkf 112
|
| Management letters CSSF 09/423 | Management letters (ML) (OPC Loi 2010, OPC Loi 2007, SICAR) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-ML-LL-0000.pdf (OPC Loi 2010) |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 82 |
| Management letters of GFI | (-) Management letters (ML) (Investment fund manager (IFM) Gestionnaire des fonds d'investissment (GFI)) (-) Letter of explanation (LE) |
DOCREP-ANNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-ML-LL-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 125 |
| Long forms CSSF 09/423 |
(-)Long Form reports (LF) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-LF-LL-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 81 |
| Fin. Rep. of GFI |
(-) Annual management company report (AR) |
DOCREP-S00001234-00000000-0000-2018-01-15-AR-EN-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 80 |
| 08/371 report not in 08/371 | (-) Auditor report (RR) (-) Report on agreed-upon procdrues to meet Hong Kong Securities (HK) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-RR-LL-0000.pdf (OPC Loi 2010) |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 88 |
| Other closing documents of GFI |
(-) Risk management function(GR)
|
DOCREP-SNNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-GR-LL-0000.pdf (IFMs) |
CSSF - Document transmission Circulars 19/708 |
bus 21 wkf 126
|
| AML_AIFM_REG Reporting |
(-) Minutes of meetings of the governing body (Board of directors or management board) (BD) |
DOCREP-ANNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-BD-LL-0000.pdf |
CSSF - Document transmission Circulars 19/708 |
bus 21 wkf 133 |
| 08/371 FIS prospectus | SIF: (-) Prospectus (PC) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-PC-LL-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 83 |
| 08/371 UCI prospectus | UCI: (-) Prospectus (PC) (-) Simplified prospectus (PS) (-) Letter of explanation (LE) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-PC-LL-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 84 |
| 08/371 FIS report | SIF: (-) Annual Report (AR) (-) Letter of explanation (LE) (-) Other periodic report (RO) (-) Movements in the securities portfolios (PM) SICAR: |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-AR-LL-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 87 |
| 08/371 report | UCI: (-) Annual Report (AR) (-) Semi-annual report (SR) (-) Letter of explanation (LE) (-) Other periodic report (RO) (-) Movements in the securities portfolios (MP) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-AR-LL-0000.pdf |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 89 |
| Management regulation/status | (-) DOCREP MR: Management Regulations of UCITS (MR) (-) DOCREP AI: Articles of Incorporation of UCITS (AI) (-)DOCREP AI: Articles of Incorporation of SICAR (AI) |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-MR-LL-0000.pdf (OPC Loi 2010) |
(-) CSSF - CIRCULAIRE CSSF 19/708 |
bus 21 wkf 108 |
| Key investor document | Key Investor Information Document |
DOCREP-ONNNNNNNN-CCCCCCCC-PPPP-YYYY-MM-DD-KI-LL-0000.pdf (OPC Loi 2010) |
(-) CSSF 11/509 (-) CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 11 |
| CSSF attestation | CSSF attestation request | - | - | bus 21 wkf 104 |
| AIF Reporting | AIFREP | AIFREP-P12345678-A00000001-F00000000-00000000-MAN-20140129145000.zip AIFREP-P12345678-A00000111-V00002222-00003333-AIF-20140129145000.zip |
CSSF - Circular 14/581 | bus 54 wkf 24 |
| Management company report | SGOREP | SGOREP-S9999-2009-03-G21-L2-S-N--.xls |
(-) CSSF - Circular 10/467 |
bus 26 wkf 95 |
| PSF report | PSFREP | PSFREP-P9999-2008-03-P11-L1-L-N--.xls |
(-) CSSF - Circular 05/178 |
bus 18 wkf 94 |
| Titrisation vehicles (=> BCL - Securitisation Vehicles reporting) |
S2.14 S2.15 TPTTBS |
S0214_L1_201412_T000000999_T000123001_20150120_001.xml S0215_L1_201412_T000000999_T000123001_20150120_001.xml TPTTBS_L1_201412_T000000999_T000123001_20150120_001.xml |
(-) Circular 2014/236 |
bus 23 wkf 98 |
| Issuing companies reporting (=> BCL - Financial Companies reporting) |
S2.16 S2.17 |
S0216_L1_201406_DSE0003524_DSE0003524_20140720_001.xml S0217_L1_201406_DSE0003524_DSE0003524_20140720_001.xml |
(-) BCL - Reporting instructions S2.16, S2.17, TPTIBS | bus 35 wkf 90 |
| Reporting securities by securities of issuing companies (=> BCL - Financial Companies reporting) |
TPTIBS | TPTIBS_L1_201406_DSE0003524_DSE0003524_20140720_001.xml | (-) BCL - Reporting instructions S2.16, S2.17, TPTIBS | bus 35 wkf 90 |
| Rapport narratif (CAA) (Companie) - Governance Re |
N01; N02; N03; N04; N07; N08; N09; N10; N11 no source files |
N01V-LU-01-20181231-CAA-LEIDéclarant-LEIDéposant.pdf | (-) Circulaire 15/10 (-) File naming convention |
bus 62 wkf 64 |
| Rapport narratif (CAA) (Réviseur) - Governance Rep |
N05; N06 no source files |
N05V-LU-01-20181231-CAA-LEIDéclarant-LEIDéposant.pdf | (-) Circulaire 15/10 (-) File naming convention |
bus 62 wkf 63 |
| Solvency II Reporting | XBRL Solvency II reports no source files |
S01V-LU-01-20181231-CAA-LEIDéclarant-LEIDéposant.pdf | (-) Circulaire 15/10 (-) File naming convention |
bus 62 wkf 44 |
| FATCA sending | FATCA | FATCA_20150520080022_F0_2016_B_1970010112345_006M8M.00000.LE.442_P.xml | bus 60 wkf | |
| CRS report | CRS | CRS_20170615114523_CRS701_2016_B_19751234567_01234567890M00000000_P.xml | (-) ACD-CRS (-) Newsletter 06/02/2017 (-) ECHA-n°4 06/02/2017 |
bus 68 wkf |
| OTHER reporting (=> CSSF) |
OTHREP | OTHREP-B9999-HELLO_WORLD.xlsx | Naming convention for CSSF reportings | bus 19 wkf 93 |
| Various correspondence (OTH) (=> BCL -OTHER reporting) |
OTXREP | OTXREP-B0nnn-BOP_IDE_2015_B0nnn_20160615_001.xls | BCL Reporting Instructions | bus 22 wkf 75 |
| Non LU UCI registration | KIID, prospectus, FactSheet... | KIIDOC-2017-12-21-EN-LU-2017-12-21-IE0012345678-12121212.pdf | - | bus 30 wkf 107 |
| Divers/Autres | tbd | tbd | - | bus 5 wkf 73 |
| SIAG (03/108) | (-) Miscellaneous (-) Miscellaneous report (-) Reponse to the CSSF |
No file name convention | - | bus 5 and 1 wkf 71 |
| Wrong name: Management company end the right name should be => Financial reports of Management companies) |
(-) Management letters (-) Annual management company report (-) Semi-annual management company report (-) Management company report, other frequency (-) Miscellaneous report (-) Response to the CSSF (-) Explanation letter (-) Auditor's report |
No file name convention | - | bus 5 and 1 wkf 80 |
| Modification société gestion | tbd | tbd | - | bus 5 and 1 wkf 70 |
| Modification group UCI | (-) Prospectus (-) Prospectus Addendum (-) Registration request (-) Incorporating documents (-) Other informational and marketing documents (-) Depositary bank agreement (-) Management agreement (-) Advisory agreement (-) Distribution agreement (-) Domiciliation agreementt |
No file name convention | - | bus 5 and 1 wkf 69 |
| Modification UCI | (-) Prospectus (-) Prospectus Addendum (-) Registration request (-) Incorporating documents (-) Other informational and marketing documents (-) Depositary bank agreement (-) Management agreement (-) Advisory agreement (-) Distribution agreement (-) Domiciliation agreementt |
No file name convention | - | bus 5 and 1 wkf 68 |
| Agrément société de gestion | tbd | tbd | - | bus 5 and 1 wkf 67 |
| UCI agreement Since 01/11/2019 the creation and transmission of the 5001 procedure via our channel is no longer possible. |
(-) Prospectus (-) Registration request (-) Incorporating document (-) Other informational and marketing documents (-) Depositary bank agreement (-) Management agreement (-) Advisory agreement (-) Distribution agreement (-) Domiciliation agreementt (-) Miscellaneous agreement |
No file name convention | - | bus 5 and 1 wkf 66 |
| Envoi de documents à la CSSF | tbd | tbd | - | bus 1 wkf 79 |
| Notification 2002/77 | tbd | tbd | - | bus 1 wkf 72 |
General tab
The General tab has to be used in the following cases:
Case 1:
(-) Transmission of all reportings that have been generated by our Report Generation module and transmitted through the Transmission button available in the form.
=> List of all reportings that can be created manually with our Report generator
Case 2:
(-) Transmission of replies to source files initiated by the supervising authorities
| Report naming convention |
Detail | Supervising authority | Circular | e-file User Guide |
|---|---|---|---|---|
| SPJ | Replies to Notification and execution of court orders 646REP 663REP 664REP |
CSSF | Circular 13/566 | How to reply to court orders issued by investigating judges of Luxembourg |
| U11 | Replies to to U11 (Global Feedback) | CSSF | (-) CSSF - Circular 15/627 (-) CSSF - Circular 12/540 (-) CSSF - File naming convention U1.1 reporting |
How to reply to U1.1 Global feedback |
| CPR, RAC, RDI, RGO,RLB, RRE, ESP, ETR, RSO,FIR |
Replies to source files received from the CAA | CAA | (-) Circulaire 15/10 (-) File naming convention |
Wiki-CAA Manual |
Solving the most common problems
Reporter is blocked
The message below is generated if your LUXTRUST e-file SSL certificate has not been registered with the CSSF.
For some reportings, the LUXTRUST e-file SSL certificate used by the reporting entity must be registered with the CSSF, before sending any files, according to the registration procedure described in the CSSF 08/334.
The LUXTRUST e-file SSL certificate must be registered with the CSSF for the below reportings:
- FINREP (CSSF circular 08/344)
- COFREP (CSSF circular 08/344)
- ESP (Special enquiries; CIRCULAR CSSF 08/344)
- PFS reporting (Other professionals of the financial sector; CIRCULAR CSSF 08/369)
- SICAR (Sociétés d´investissement en capital à risque)
- Bank Reporting (CIRCULAR CSSF 10/457; CIRCULAR CSSF 15/624)
- Management companies (CIRCULAR CSSF 10/467)
- Payment institutions (CIRCULAR CSSF 11/511)
- Electronic money institutions (CIRCULAR CSSF 11/522)
- OTHER reporting
- AIFMD reporting (CIRCULAR CSSF 14/581)
=> e-file User Guide: CSSF Certificate registration - General
=> e-file User Guide: CSSF Certificate registration - AIFMD
Write rights
The Transmission Module requires read AND write access on the e-file directory in order to run properly.
These error messages reflect access problems.
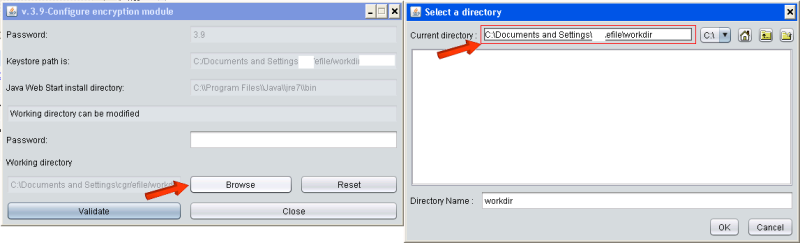
How to retrieve the path of your e-file directory:
1. Connect to e-file v1
2. Click the link Configure my workstation security
3. Click the link Configure the encryption module
4. A Java windows opens, click Browse
5. The path of the e-file directory will be written here :
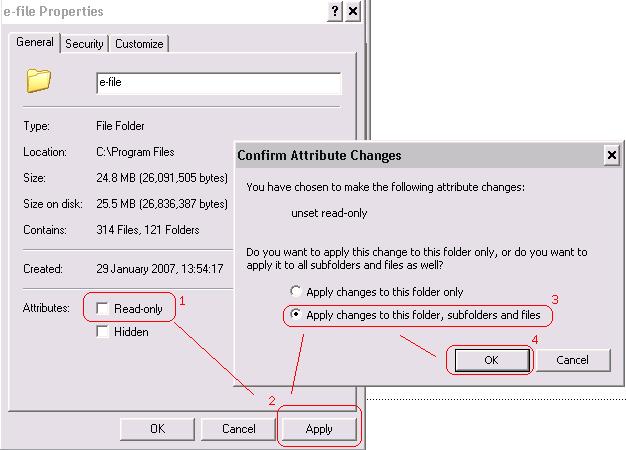
In order to get read AND write access on the e-file directory, please follow the steps below:
Right click on the e-file directory > properties ... > disable the checkbox label 'Read Only'
If your internal security allows that action, you must also adapt your user rights to all e-file sub-directories.
Note: If you are not allowed to perform such an action, we invite you to contact your IT department so that they can do it for you.
Firefox and Safari compatibility
The default installation of Firefox and Safari with mac needs some tweek in order to work :
firefox
When the transmission module starts, Firefox will download the EFileCrypto.jnlp file but add .html at the end. In order to start it, you need to remove the .html at the end of the file.
Safari (mac)
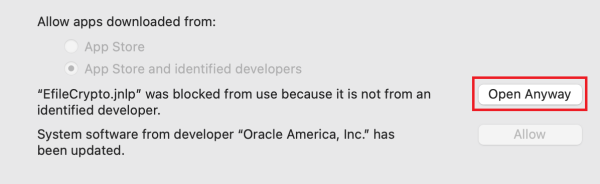
On Mac you might have an error message when you try to start the EFileCrypto.jnlp file stating that it belongs to a "unauthorized developper"
If you have this message, you will need admin right on the machine : Go to : Mac icon -> System preference -> Security & Privacy
On this screen you have to select "Open Anyway"
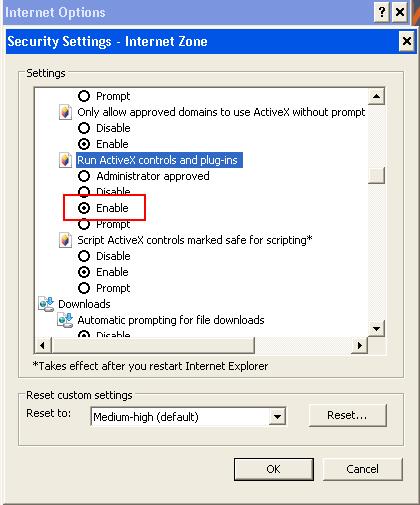
Running ActiveX
The Transmission Module needs the ActiveX controls and plug-ins to be enabled. This association is automatically set up when installing Java, but sometimes a specific Internet Explorer option may prevents it to run properly.
Solution:
1. In Internet Explorer, navigate to Tools > Internet Options.
2. On the Security tab, select a network zone.
3. Click Custom Level.
4. Scroll down to the Run ActiveX controls and plug-ins.
5. Select the checkbox label Run ActiveX controls and plug-ins.
6. Click OK and click Apply.
Teamviewer
Click the link below in order to get remote assistance:
(-) Get remote assistance Windows compatible executable
(-) Get remote assistance MAC compatible executable
KeyTool
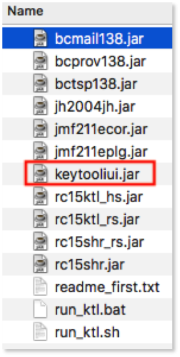
KeyTool is an independent Java software which can be downloaded by clicking the link below:
To open it, double click on keytooliui.jar
Why to merge two keystores
While renewing a Luxtrust certificate, the Transmission Module sometimes creates a new keystore file instead of amending the existing one. This happens when the existing keystore is not selected during the keys generation. The new keystore then allows all E-file functionnalities. However, documents encrypted with or for one of your old certificates cannot be opened.
This article explains how to merge two keystores.
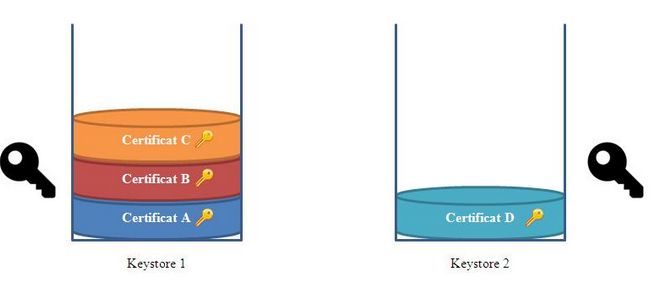
How does a keystore work
Keystore is a Java technology that keeps an history of your certificates like a stack. It is a small file which extension is ".ks" and contains a list of certificates.
Every certificate contains a public key but also a private key which is protected by a password (symbolized ![]() ). The keystore access is protected by a password as well (symbolized
). The keystore access is protected by a password as well (symbolized ![]() ). The private key password and the keystore password must always match, thus
). The private key password and the keystore password must always match, thus ![]() =
= ![]() . For this reason make sure to always use the same password while handling the keystore.
. For this reason make sure to always use the same password while handling the keystore.
During encryption or decryption, the Transmission Module will browse the different keystore's certificates in order to find the associated private key. That's why it's better to have all your company's certificates inside the same keystore.
On the previous sketch, the certificate D has been inserted in a new keystore (keystore 2). For convenience reasons, we prefer putting it in the other keystore (keystore 1) at the top of the pile.
How to merge two keystores
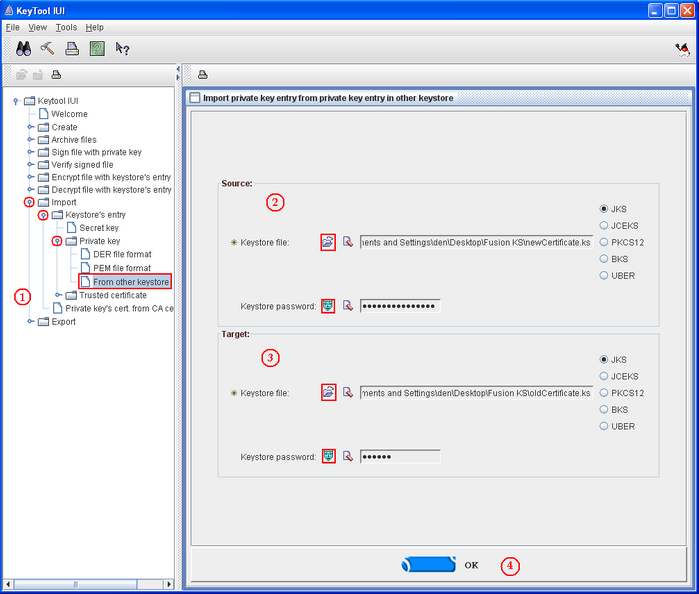
The merging of two keystores is done thanks to an independent Java software called KeyTool which can be downloaded at the following link : [[1]]. To open it, double click on keytooliui.jar.
Follow all the steps to import public and private key from a certificate to another.
- Select "Import private key from other keystore" as shown on the above printscreen (step 1)
- Click on the two icons in the "Source" section in order to select the keystore containing the certificate to import (step 2). The source keystore corresponds to Keystore 2 of the "How does a keystore work" section sketch.
- Do the sane for the target section that selects the keystore on which import the certificate (step 3). The target keystore corresponds to the Keystore 1 of the of the "How does a keystore work" section sketch.
- Click OK (step 4)
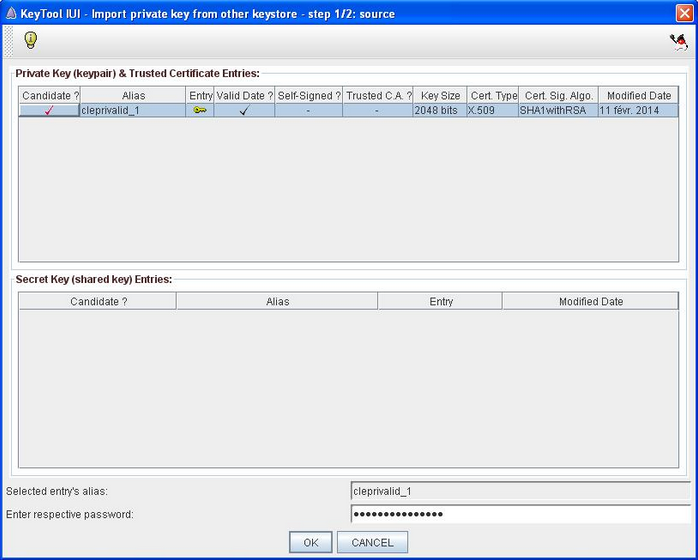
- Select the certificate (that contains the private key) of the source keystore that you desire to import, input its password in the specific field at the bottom of the window.
Click OK
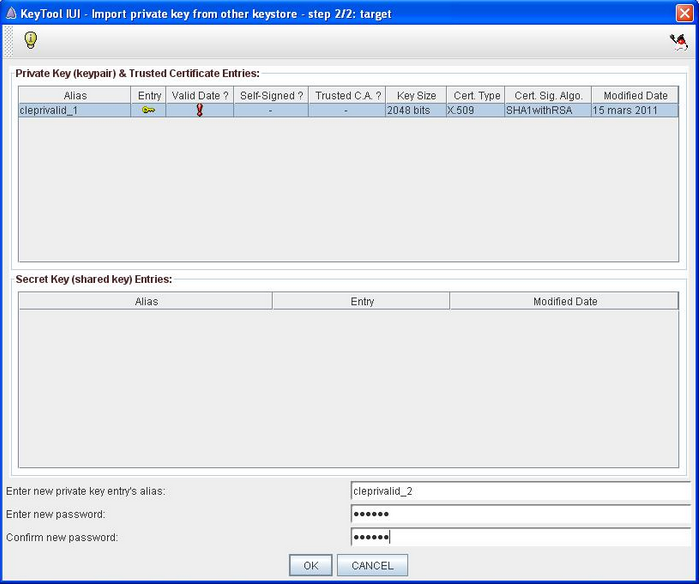
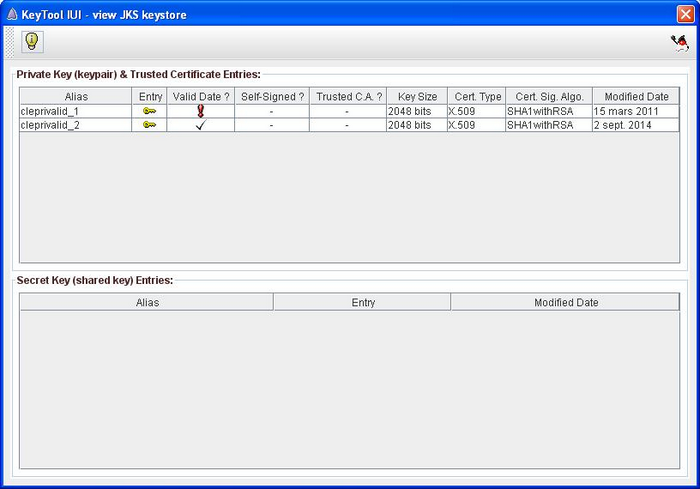
Input the name of the new private key that will be generated in the target keystore. The naming convention is :
cleprivalid_ + incremented number.
As an example, if the target keystore contains already 4 certificates, it has the following entries :
- cleprivalid_1
- cleprivalid_2
- cleprivalid_3
- cleprivalid_4
The new key name will be cleprivalid_5.
- Input the password that will be associated to the new key. Warning : it must be the same as the other private key's password of the target keystore (the one of the keystore). Confirm password.
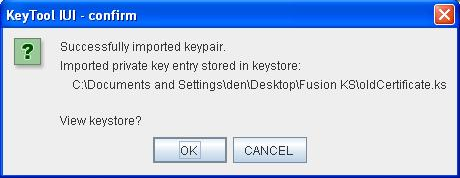
- Click Ok
The following window appears to indicate the success of the import. When clicking Ok you will see the target keystore content that should contain the imported certificate.